#
NIST Framework for Improving Critical Infrastructure Cybersecurity
#
Acronyms, Abbreviations, and Initialisms
#
Overview
The National Institute of Standards and Technology developed the "Framework for Improving Critical Infrastructure Cybersecurity," which describes a voluntary risk management framework ("the Framework") that consists of standards, guidelines, and best practices to manage cybersecurity-related risk. The Framework's prioritized, flexible, and cost-effective approach helps to promote the protection and resilience of critical infrastructure and other sectors important to the economy and national security.
This framework is ideal to use as a supplement to best coding practices and code reviews and testing, but also functions as an approach to risk mitigation.
#
Components
The Cybersecurity Framework consists of three main components:
Core Implementation Tiers Profiles
The Framework Core provides a set of desired cybersecurity activities and outcomes using common language that is easy to understand. The Core guides organizations in managing and reducing their cybersecurity risks in a way that complements an organization’s existing cybersecurity and risk management processes.
The Core includes five high level functions:
- Identify (ID)
- Protect (PR)
- Detect (DE)
- Respond (RS)
- Recover (RC)
Spread across these five functions are 23 categories.
The image below depicts the Framework Core's Functions and Categories:
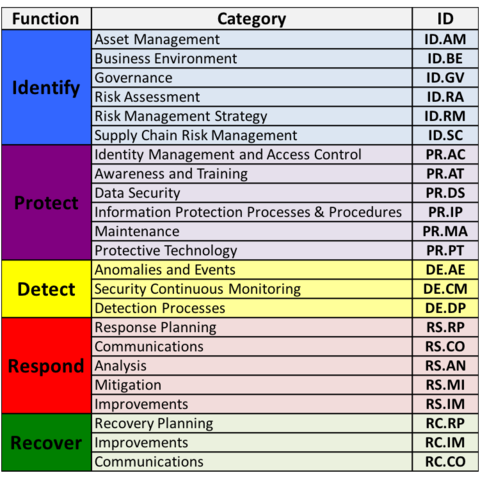
The Framework Implementation Tiers assist organizations by providing context on how an organization views cybersecurity risk management. The Tiers guide organizations to consider the appropriate level of rigor for their cybersecurity program and are often used as a communication tool to discuss risk appetite, mission priority, and budget.
Framework Profiles are an organization’s unique alignment of their organizational requirements and objectives, risk appetite, and resources against the desired outcomes of the Framework Core. Profiles are primarily used to identify and prioritize opportunities for improving cybersecurity at an organization.
#
Noteworthy
#
Sources
- https://www.nist.gov/publications/framework-improving-critical-infrastructure-cybersecurity-version-11
- https://www.nist.gov/cyberframework/getting-started
- https://www.nist.gov/cyberframework/online-learning/components-framework

